When you start ReqView the first time, the application starts a New User Tour and opens the DEMO project to help you get started with ReqView more easily. To open the DEMO project later, click Help and select Example Project. You can edit the DEMO project without any limitation, even with the FREE plan.
The main purpose of the DEMO project is to provide new users a working example how to specify and manage requirements for a SW development project in ReqView. The project is not complete.
The DEMO project describes user needs, standard security requirements, risks, SW requirements, verification tests and solution architecture for a simplified functionality of ReqView application. See the following diagram illustrating project documents and types of traceability links:
Project Data Model:
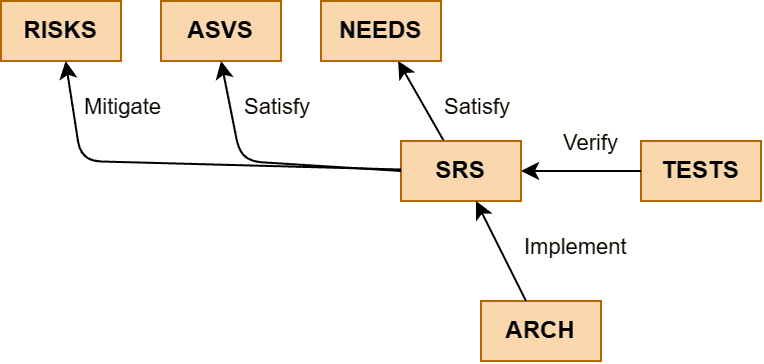
Documents:
- NEEDS: User Needs – the highest level user needs described as user stories and constraints, see also User Stories Example and User Stories Template
- ASVS: Application Security Verification Standard – security requirements specified by the OWASP ASVS Standard, see also ASVS Template
- RISKS: Failure Mode and Effects Analysis – assessment of information security risks using the FMEA method, see also FMEA Template
- SRS: Software Requirements Specification – low-level SW requirements derived from user stories or from corrective actions mitigating project risks, see also SRS Example and ISO/IEC/IEEE 29148 Templates
- TESTS: Verification Tests – test cases verifying functionality described by the SW requirements
- ARCH: Architecture – the architecture of the application described by the SW requirements
Traceability:
- Satisfy – satisfaction links leading from downstream SW requirements to the related highest level user needs and standard security requirements
- Mitigate – mitigation links leading from downstream SW requirements to the related corrective action of a project information security risk
- Verify – verification links leading from test cases to the related SW requirements
- Implement – implementation links leading from SW components in the SW architecture to the related SW requirements
Dashboard:
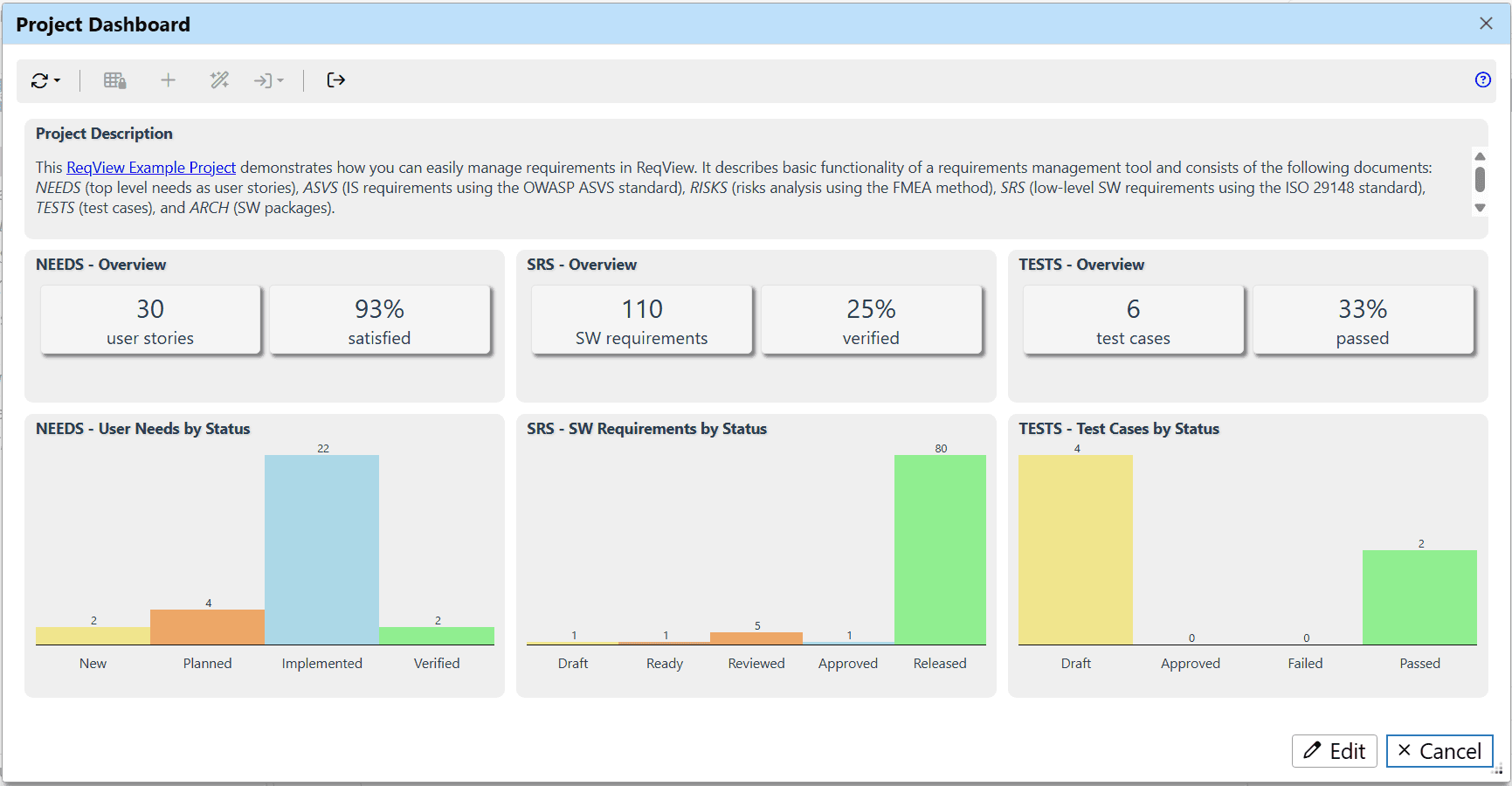
- Project Description – the project description.
- NEEDS - Overview – the count of user stories (NEEDS) and the percentage of user stories satisfied by SW requirements (SRS).
- SRS - Overview – the count of SW requirements (SRS) and the percentage of SW requirements verified by tests (TESTS).
- TESTS - Overview – the count of test cases (TESTS) and the percentage of passed test cases.
- NEEDS - User Needs by Status – the chart showing the count of user stories (NEEDS) having the given value of attribute Status.
- SRS - SW Requirements by Status – the chart showing the count of SW requirements (SRS) having the given value of attribute Status.
- TESTS - Test Cases by Status – the chart showing the count of test cases (TESTS) having the given value of attribute Status.